
|
|
ENCYCLOPEDIA OF RADIO ELECTRONICS AND ELECTRICAL ENGINEERING Security alarm system on KR1850BE35. Encyclopedia of radio electronics and electrical engineering
Encyclopedia of radio electronics and electrical engineering / Safety and security The proposed system is designed to protect objects equipped with sensors, the contacts of which open when triggered. It is possible to arm an object and disarm it, listen to noises and other sounds in protected premises, detect attempts to close the wires going from the sensors to the system board. A fire alarm can be entered into the device. Simplification of the system (compared to other devices with a similar set of functions) was achieved by using a single-chip micro-computer (microcontroller) KR1850BE35. Up to 64 sensors can be connected to the described security system, and 16 wires are enough to connect them to the controller - eight group and eight bit lines (Fig. 1).
Sensors B1-B64 are located in secure premises, the rest of the nodes (including the system board, the schematic diagram of which is shown in Fig. 2) - in the controller unit installed at the workplace of the operator on duty. To interrogate sensors, group (S1-S8) and bit (S9-S16) switches are alternately closed by signals G1-G8 and P1-P8 from the system board, and at each moment only one of S1-S8 and one of S9 - S16 is closed. Schematic diagram of the group key is shown in fig. 3.a, bit - in fig. 3b. As you can see, both of them are assembled on two transistors, the functions of the actual keys are performed by transistors VT2.
Each of the protected objects is equipped in accordance with the scheme shown in Fig. 4. The sensor can be of any type (mechanical, radar "infrared, ultrasonic), it is only important that when triggered, the contacts S1 of its output circuit open. In addition, resistors R1 and R2 and a diode VD1 are required. Everything else is mounted if necessary. Node S1R1R2 must be designed in such a way as to exclude an intruder's access directly to the S1 contacts.In this case, all attempts to block the sensor by "shorting" the wires going to it will be fixed by the system.This property can be used to connect (as shown by the dashed line) normally open contacts 52 of the fire alarm sensor.The signal "Short circuit" supplied by the controller will also be the signal "Fire". True, it will be possible to find out exactly what happened only, as they say, "personally arriving at the place."
The BM1 microphone and the A1 amplifier are designed for the operator to listen to noises in a protected area. The type and circuit diagram of the amplifier are not given - they may be different depending on the selected microphone, the required sensitivity, etc. It is important that the constant component of the voltage at the output of the operating amplifier is sufficient to open the VD2 diode, through which the sound signal is common to all AK circuit sensors (acoustic control) enters the UMZCH input. The VAK pulse generated by the controller (switching on acoustic control) arrives simultaneously at all sensors, but only one of them reacts to it. which is currently 'selected' by the closed group and bit keys. As a result, its transistor VT1 opens, the collector current flows through the LED of the optocoupler U1, the photothyristor of the optocoupler opens, and the power supply voltage is applied to the amplifier A1. The amplifier remains on as long as the OAC circuit (disabling acoustic control) will not be momentarily interrupted in the controller, which will lead to the closing of the thyristor. Let's return to the circuit diagram of the controller motherboard (see Fig. 2). Its basis is the KR1850BE35 (DD2) microcontroller, the control program of which (see table) is stored in the DD13 PROM. The microcontroller accesses the external program memory, generating the PME signal. Microcircuits DD7 and DD9 form an address register, which is written to by the ALE signal. moreover, the microcontroller outputs the upper bits of the address through the bits P20-P23 of its port P2. A small number of peripheral registers made it possible, by eliminating the decoder, to use separate bits of the address bus for their selection. The microcontroller accesses registers at addresses:
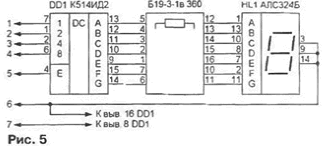
The output signals of the control register DD8 turn on and off the polling of sensors (Q0), as well as indicators of operational information (Q1), arming (Q2) and disarming (Q3). An alarm is generated at the output Q4 of this register, and Q5 controls the electronic key (transistors VT1, VT2). signaling the activation of acoustic control. Two cells of digital indicators H12 - H6 are connected to the outputs of the registers of operational (DD1) and constant (DD4) information. They are made according to the scheme shown in Fig. 5.
The microcontroller sequentially interrogates the sensors, outputting the codes of their numbers to port P1. In accordance with them, the decoders DD14 and DD15 generate polling signals G1 - G8, P1 - P8. The state of the sensor located at the intersection of the group and bit lines, the keys of which are currently closed, is determined by the voltage drop across it, created by the current flowing through the circuit (see Fig. 1): power supply + 12 V, measuring resistor R1, closed group key, sensor, closed bit key, common wire. In the initial state (in the absence of an alarm), the resistance of the sensor and the voltage falling on it are small (but not equal to zero), when triggered, they are large. The inputs of comparators DA1 and DA2 are connected to the connection point of the measuring resistor with group keys (circuit M). The response threshold of the first of them is 8 V and lies between the voltage levels corresponding to the triggered and non-operated sensors. The DA2 comparator responds to an input voltage of less than 6,8 V, i.e., below the level characteristic of failed sensors. This allows you to fix the short circuits of the lines suitable for the sensors. If necessary, the comparator thresholds can be changed by selecting resistors R7 and RXNUMX. An emergency situation (alarm) is recorded when any of the comparators is triggered and there is a mark in the internal RAM of the microcontroller that this room is armed. The RNC signal, which turns on the siren or other actuator, is given only upon confirmation of the sensor operation 20 ms after its first detection. At the same time, the HL3 LED (“Alarm”) turns on. and if the comparator DA2 has worked, then the HL2 LED ("Short circuit") also turns on. The sensor number is displayed on the digital indicator of operational information (NC, H4) and stored in the internal register R20 of the microcontroller. In addition, a VAC signal with a duration of approximately 20 ms is applied, which turns on the microphone amplifier in the room where the sensor was triggered. The alarm continues for 3 s. after which only the number of the triggered sensor, transferred to the indicator of constant information (H1, H2), indicates an emergency situation. If the SA1 switch contacts are open, the CPH signal will remain active even after the three second interval has elapsed. Disable it by transferring SA1 to the closed position. The permanent information indicator can be extinguished by pressing the SB9 ("Reset") button. Her second contact group breaks the UAC circuit, turning off listening to the protected premises. While the indicator is not extinguished, the microcontroller, having detected a triggered sensor, compares its number with that stored in register R20. If they match, no new events will occur, and if not (another sensor has triggered), an alarm will be generated again. Several simultaneously triggered sensors are processed one by one, starting with the one with the smallest number. It is he who will be fixed in the register R20 and will be displayed on the indicator of constant information. Every 3 seconds, an alarm will sound, and the number of the next triggered sensor will appear on the operational information indicator. The security system is controlled by commands, the codes of which the operator dials using the SВ2-SВ6 buttons. The command code is a two-digit decimal number, in the most significant digit of which is the digit N, which matches the XI-X4 jumpers specified in binary form. On the circuit diagram (see Fig. 2), they are shown in the position corresponding to the number 5. If necessary, it can be easily changed by rearranging the jumpers. The following commands are available: N0 - arm the premises; N1 - disarm the premises; N2 - check if the premises is armed; N3 - alternately show on the indicator the numbers of all premises taken under protection; N4 - arm all premises; N5 - disarm all premises. The first three commands require preliminary dialing of the room (sensor) number. To do this, press one or several buttons SВ2-SВ6 simultaneously so that the sum of their values is equal to the most significant digit of the number. The entered digit will be shown in the least significant digit of the operating information indicator and stored in the memory of the microcontroller, although the indicator will turn off after the buttons are released. Enter the second digit in the same way. It will appear in the low digit of the indicator, and the previously entered one in the high digit. If a mistake is made, it is enough to repeat everything from the beginning, entering the correct values. After the correct number is dialed, press the button SB7 ("VD- - data entry"). Command codes are typed in the same way, but they are entered by pressing the SВ8 button ("ВК" - command input). The mode of the selected room is displayed by the LEDs HL4 ("Unarmed") and HL1 ("Unarmed"). Execution of arming and disarming commands leads to a change in the state of the corresponding bits of the internal RAM of the microcontroller. The command to sequentially display the numbers of the premises taken under protection does not make any changes in the RAM. Button SB1 ("Set 0") is designed to restart the controller and is mainly used for device debugging and troubleshooting. However, if you press it simultaneously with the SB6 ("0") button, all premises served by the system will be disarmed. Author: R. Trunin, Kazan
Air trap for insects
01.05.2024 The threat of space debris to the Earth's magnetic field
01.05.2024 Solidification of bulk substances
30.04.2024
▪ Skyrmions will increase the capacity of the hard drive by 20 times ▪ Graphene airgel is lighter than air ▪ A tomograph is more efficient than a polygraph ▪ Dell Latitude 7212 Rugged Extreme Tablet Rugged Tablet ▪ Electronic cigarettes harm lung immunity
▪ section of the site Power supply. Article selection ▪ article I approve! Popular expression ▪ article What is archeology? Detailed answer ▪ Sassafras officinalis article. Legends, cultivation, methods of application ▪ article Magician's assistants. Focus Secret
Home page | Library | Articles | Website map | Site Reviews www.diagram.com.ua |






 Arabic
Arabic Bengali
Bengali Chinese
Chinese English
English French
French German
German Hebrew
Hebrew Hindi
Hindi Italian
Italian Japanese
Japanese Korean
Korean Malay
Malay Polish
Polish Portuguese
Portuguese Spanish
Spanish Turkish
Turkish Ukrainian
Ukrainian Vietnamese
Vietnamese





 Leave your comment on this article:
Leave your comment on this article: