
|
|
ENCYCLOPEDIA OF RADIO ELECTRONICS AND ELECTRICAL ENGINEERING
Telephone line security. Encyclopedia of radio electronics and electrical engineering
Encyclopedia of radio electronics and electrical engineering / Security devices and object signaling Heads of various organizations, entrepreneurs and other business people cannot do without a telephone. Quite often they communicate, make various decisions, and clarify emerging issues using the telephone, so it is not surprising that they want to make sure that conversations are not available to outsiders. However, it should be noted that today in the market of technical means you can see many types ofdevices for intercepting telephone messages both domestic and foreign manufacturers. Methods for intercepting telephone messages There are six main listening areas on a telephone line. These include: - telephone set; - telephone line, including junction box; - cable zone; - ATS; - multichannel cable; - radio channel. A diagram of a telephone line with listening zones is shown in fig. 122.
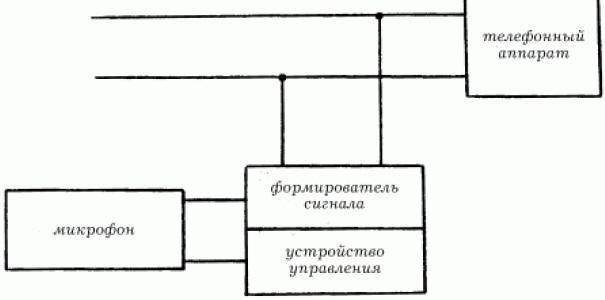
It is easiest to connect in the first three zones. For listening, a parallel device is most often used. In the cable zone, connection is more difficult, since for this you need to penetrate the telephone communications system, consisting of pipes with cables laid inside them, and choose the right pair among many others. Telephone repeaters Telephone radio repeaters are radio extenders for transmitting telephone conversations over radio channels. Bookmarks installed in phones are automatically activated when you pick up the handset and transmit information to the interception and recording point. The radio transmitter is powered by the telephone network voltage. Due to the lack of batteries and microphone in the repeater, it may be small in size. The disadvantages of these devices include the fact that they are easy to detect by radio emission, therefore, to reduce the probability of their detection, the radiation power of the transmitter installed on the telephone line is reduced. A powerful repeater is installed in a separate room. It re-radiates the signal in encrypted form. Radio repeaters can be made in the form of capacitors, filters, relays and other standard units and elements that are part of telephone equipment. To listen to the telephone line, it is possible to use a telephone with a radio extender consisting of two radio stations. The first is located in the handset, the second - in the telephone. The receiver is tuned to the desired frequency. Room eavesdropping With the help of a telephone line, you can also listen to the premises. For this, special devices are used. A diagram of possible listening to premises via a telephone line is shown below (Fig. 123).
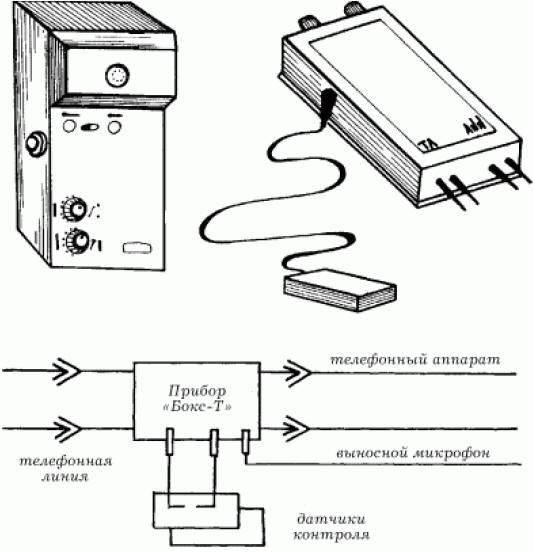
The principles of operation of such a device are as follows: the subscriber's number is dialed. The first two beeps are absorbed by the device, i.e. the phone does not ring. The handset is placed on the lever, and after a minute they begin to dial the same number again. After that, the system enters listening mode. On fig. 124 shows one such device.
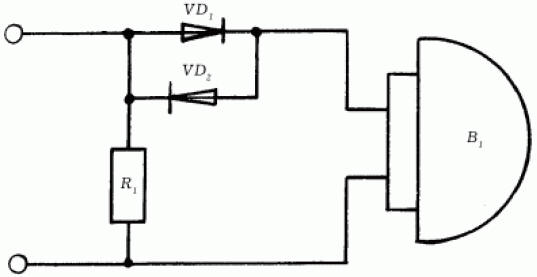
"Box-T" is able to control the room by phone at any distance. There are also no-way systems for transmitting acoustic information over telephone lines, which make it possible to listen to premises without installing any additional equipment. Technical means of information protection Regardless of what kind of activity a person is engaged in, for example, whether he is the head of a large enterprise or a commercial bank, he will certainly be interested to know how information can be leaked and how to protect himself from it. Protection of telephone sets and communication lines The telephone has long become an integral part of human life, telephone lines carry a variety of information flows, and that is why it is important to protect them from being used to harm. The telephone set and the PBX communication line are the main channels for information leakage. 1. Changes are made to the design of the phone to transmit information or special equipment is installed with high-frequency radiation in a wide frequency band, modulated by an audio signal, which serves as a channel for information leakage. 2. The shortcomings of the designs of telephone sets are taken into account and are used to obtain information. 3. There is an external influence on the phone, as a result of which information is leaked. Phone Protection Ring chain protection. An information leakage channel may occur due to electro-acoustic conversion. When talking in a room, acoustic vibrations act on the pendulum of the bell connected to the armature of the electromagnetic relay. Sound signals are transmitted to the anchor, and it makes micro-oscillations. Further, the vibrations are communicated to the anchor plates in the electromagnetic field of the coils, as a result of which microcurrents appear, modulated by sound. The amplitude of the EMF induced in the line, in some types of telephone sets, can reach several millivolts. For reception, a low-frequency amplifier with a range of 300-3500 Hz is used, which is connected to the subscriber line. To protect the ringing circuit, a device with the circuit shown in Fig. 125.
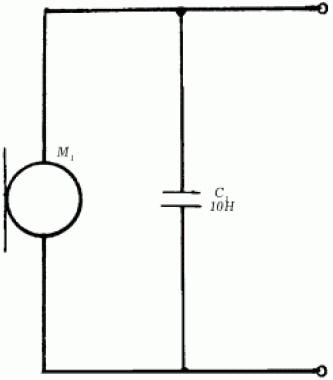
Silicon diodes are connected in anti-parallel to the bell circuit of telephone set B1. A dead zone for micro-EMF is formed, which is explained by the fact that in the range of 0-0,65 V the diode has a large internal resistance. Therefore, low-frequency currents induced in the apparatus circuit will not pass into the line. At the same time, the subscriber's audio signal and the call voltage freely pass through the diodes, since their amplitude exceeds the opening threshold of the diodes VDl, VD2. Resistor R1 is an additional noisy element. Such a circuit, connected in series to the communication line, suppresses the micro-EMF of the coil by 40-50 dB (decibels). Microphone circuit protection Receiving information through the microphone circuit is possible due to the method of high-frequency imposition. The scheme for protecting the microphone device using this method is shown in fig. 126.
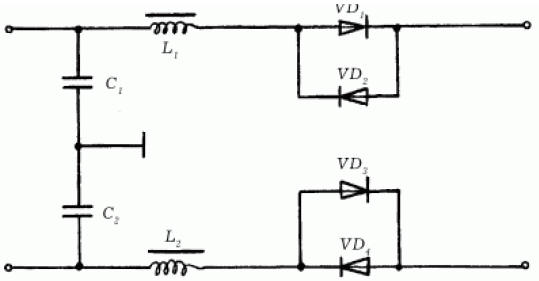
Microphone M1 is a modulating element, for the protection of which it is necessary to connect a capacitor C1 with a capacity of 0,01-0,05 μF in parallel with it. In this case, capacitor C1 shunts the microphone capsule M1 at high frequency. The modulation depth of high-frequency oscillations is reduced by more than 10 times, which makes further demodulation almost impossible. Comprehensive protection scheme The integrated protection scheme includes the constituent elements of the first and second schemes above. In addition to capacitors and resistors, this device also contains inductors (Fig. 127).
Diodes VD1-VD4, connected in anti-parallel, protect the ringing circuit of the phone. Capacitors and coils form filters C1, L1 and C2, L2 to suppress high frequency voltages. Details are mounted in a separate case by surface mounting. The device does not need to be configured. At the same time, it does not protect the user from direct eavesdropping by direct connection to the line. In addition to all these schemes, there are others that are close to similar devices in their technical characteristics. Many of them are designed for complex protection and are often used in practice. Cryptographic methods and means of protection To prevent listening to conversations on a telephone line, you can use a cryptographic method, which is perhaps the most cardinal measure of protection. There are two methods: 1) conversion of analog speech parameters; 2) digital encryption. Devices that use these methods are called scramblers. An analog scrambler involves changing the characteristics of the original audio signal in such a way that it becomes unintelligible as a result, while at the same time occupying the same frequency band. This allows it to be transmitted over conventional telephone communication channels. The signal change is manifested in the following: - frequency inversion; - frequency permutation; - temporary change. A digital scrambler involves changing the characteristics of the original audio signal so that it becomes unintelligible as a result. This device contributes to the preliminary conversion of an analog signal into a digital form. After that, the signal is encrypted using special equipment. Author: Korshevr N.G.
Artificial leather for touch emulation
15.04.2024 Petgugu Global cat litter
15.04.2024 The attractiveness of caring men
14.04.2024
▪ The best decisions are made on an empty stomach ▪ New series of wet tantalum capacitors with maximum capacitance ▪ Pleasure centers help the immune system
▪ section of the site Protection of electrical equipment. Article selection ▪ article The question is, of course, an interesting one. Popular expression ▪ article Which mammals have a social organization like an ant's? Detailed answer ▪ Ammi's article is great. Legends, cultivation, methods of application
Home page | Library | Articles | Website map | Site Reviews www.diagram.com.ua |






 Arabic
Arabic Bengali
Bengali Chinese
Chinese English
English French
French German
German Hebrew
Hebrew Hindi
Hindi Italian
Italian Japanese
Japanese Korean
Korean Malay
Malay Polish
Polish Portuguese
Portuguese Spanish
Spanish Turkish
Turkish Ukrainian
Ukrainian Vietnamese
Vietnamese

 Leave your comment on this article:
Leave your comment on this article: