
|
|
ENCYCLOPEDIA OF RADIO ELECTRONICS AND ELECTRICAL ENGINEERING High security digital lock. Encyclopedia of radio electronics and electrical engineering
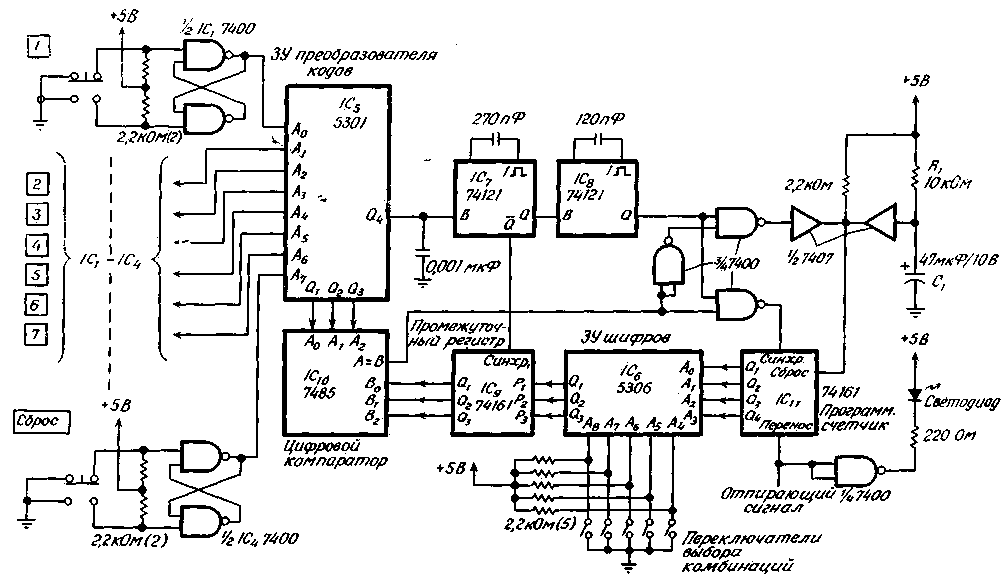
Encyclopedia of radio electronics and electrical engineering / Security devices and object signaling No tricks will help the burglar open the 15-bit digital lock with electronic blocking described below. When selecting at a speed of one combination in 10 s, it will take about 1,5 million years to randomly find the correct code. The job of a potential attacker is made even more difficult by the fact that the circuit is automatically reset when any wrong combination is entered. In this case, it is required to resume the set order, which makes it impossible to use any ordered trial and error method. The circuit contains a PROM with a capacity of 512x4 bits, in which, in addition to the correct one, 32 more combinations can be placed, which will allow you to periodically change the cipher by simply switching them. The circuit compares the input combination sequentially digit by digit with the code stored in memory, and, if the cipher is completely correctly typed, sets the output to a high TTL level. Before dialing, you must press the reset button, while the circuit is set to a state of readiness for entering the first digit. The operator also presses this button if, in his opinion, a mistake has been made in the cipher suite. The circuit allows only eight inputs (reset and seven numbers) to be encoded, since each binary word contains 3 bits. However, it is convenient to use a standard set of buttons with numbers from 0 to 9 and use one, two and three free buttons (in this case 0, 8 and 9) to reset. In this case, the degree of secrecy of the lock is increased, since only a person who knows in advance knows which buttons are used to reset. RS-flip-flops assembled on IC1-IC4 quad valves are used to suppress contact vibration in single-pole two-position pushbutton switches. Encoding of the input numbers is carried out by the integrated circuit IC5, which is a PROM type 5301 from Monolithic Memories Inc. with a capacity of 256X4 bits, programmed in accordance with the truth table (Table 1).
The specified IC was chosen to simplify the programming process, since its initial state corresponds to a logical 1, and with a reset output code of 111, most address buses have a logical 1 potential. The cipher code is programmed in IC6 memory, which is a PROM type 5306 from Monolithic Memories Inc. with a capacity of 512X4 bits. The cipher switches shown in the figure set the logical potentials on the buses of the five most significant address bits (A4-A8), choosing one of 32 combinations. By remotely programming five of these tires, you can temporarily close access to the lock to persons who know the cipher, or change combinations for security purposes. Synchronization of the circuit is carried out using two waiting multivibrators. When one button or a combination of them is pressed, a high potential is formed at the output of the most significant bit (Q4) of IC5 memory, which acts as a code converter, which starts the first waiting multivibrator IC7. The leading edge of its output potential Q, the binary word from the combination memory output IC6 is written to the intermediate memory, which is a 4-bit programmable binary counter. After 375 ns, the rising edge of potential Q at the output of multivibrator IC7 starts the second waiting multivibrator IC8. For 165 ns, when the output of multivibrator IC8 is high, the 4-bit absolute value comparator IC10 compares the input word with the stored word. If the words at the outputs of IC5 and IC6 are identical, the voltage at output A, equal to the voltage at output B of the comparator, goes high, as a result of which the program counter IC11, another 4-bit binary counter, is incremented through the NAND gates. When the words are different, the program counter is reset and the combination must be re-entered. After entering the correct combination, the contents of the program counter reaches 15 and the output of the transfer forms a high logic potential. When this unlocking potential is formed, the indicator on the LED turns on. The triggering potential drives an external TTL IC or, after appropriate amplification, a solenoid lock. When the power is turned on, the program counter can be in an arbitrary initial state. In order to prevent the lock from opening in the event of intermittent power failures, the program counter resets within the first few milliseconds after power-up by means of a reset circuit consisting of an R1 C1 charge circuit and a buffer amplifier. With a lower degree of secrecy, the circuit can be simplified, reducing the number of components and cost. In this case, instead of ICs, a priority encoder is used, for example, type 74147, but then automatic reset is excluded when two or more buttons are pressed simultaneously. You can also eliminate the power-on reset circuitry and use a smaller memory when there is no need to store 32 different combinations. The scheme can be greatly simplified by switching to 2-bit words. Then it will take 4,5 years to randomly guess the cipher when typing a combination of 15 characters in 10 seconds. Masking three input numbers in a group of buttons from 0 to 9 increases the degree of secrecy many times over. The system is expandable - the length of the word (and hence the number of inputs) and the length of the combination can be selected according to the requirements of the consumer.
In table. Figure 2 shows the contents of the PROM for the combination 174265537172443. Each combination of 15 numbers occupies 16 bits of memory, and the last bit is not used. As noted above, this arrangement is favorable for programming the output pattern 111 (with the zero value of the first address, the 16th bit is present in every 2n-1 address, where n>3, i.e. 15, 31, 63, etc. .). In this case, after unlocking the lock, the reset is carried out automatically by pressing any button. Author: D. Platteter; Publication: N. Bolshakov, rf.atnn.ru
Artificial leather for touch emulation
15.04.2024 Petgugu Global cat litter
15.04.2024 The attractiveness of caring men
14.04.2024
▪ Microbes in a squirrel wheel ▪ The material is 10 times stronger than steel
▪ section of the site Consumer Electronics. Selection of articles ▪ Flower coffee article. Popular expression ▪ article Why do muscles hurt after exercise? Detailed answer ▪ Article Chief Nurse. Job description ▪ article Powerful FET switch, 20 amps. Encyclopedia of radio electronics and electrical engineering
Home page | Library | Articles | Website map | Site Reviews www.diagram.com.ua | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||






 Arabic
Arabic Bengali
Bengali Chinese
Chinese English
English French
French German
German Hebrew
Hebrew Hindi
Hindi Italian
Italian Japanese
Japanese Korean
Korean Malay
Malay Polish
Polish Portuguese
Portuguese Spanish
Spanish Turkish
Turkish Ukrainian
Ukrainian Vietnamese
Vietnamese
 Leave your comment on this article:
Leave your comment on this article: