
|
|
ENCYCLOPEDIA OF RADIO ELECTRONICS AND ELECTRICAL ENGINEERING Protect your data! Encyclopedia of radio electronics and electrical engineering
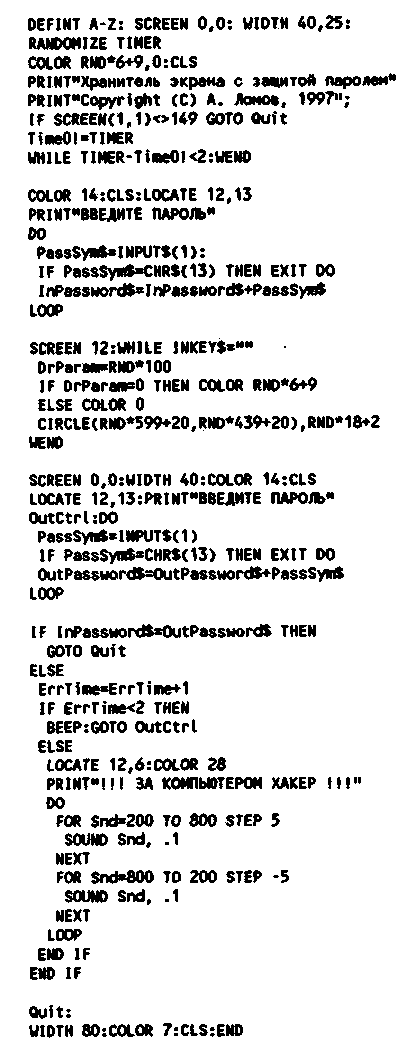
Encyclopedia of radio electronics and electrical engineering / Security devices and object signaling Today, when information has become a commodity, and computer technology is publicly available, it is necessary to protect data from possible unauthorized access. At large enterprises that have special personnel for this, the problems of effective protection both on individual PCs and in local networks have long been and reliably resolved. But the hard drive of a computer located in the office of a small firm or at home can sometimes also contain very important or even secret (from competitors) data. This article describes some simple and easy-to-implement techniques that allow users of ordinary IBM-compatible computers to prevent unwanted leaks and loss of information. Before proceeding to the practical side of the matter, it is necessary to understand from whom the data has to be protected. First of all, from strangers who accidentally or intentionally find themselves near your computer and show excessive curiosity. “Our friends” can also potentially be dangerous - through negligence, and sometimes intentionally (say, after a quarrel), they can damage or delete two or three files from the hard drive, perhaps even without suspecting their importance. But any defense is useless when professionals get down to business. So, if the “competent authorities” are interested in the stored data, they will read and decrypt it in any case. True, this procedure may cost them more than all the secrets of your company combined. PASSWORD LOGIN When working in a crowded office, where strangers are often present, you first need to set a password to start the computer. This will prevent access to it by people who do not know the password. Naturally, everyone who uses the same computer “legally” should know it. Such protection is not very reliable and protects data only from those who do not know its intricacies. However, in an apartment or small business setting, the techniques described in this and the next two sections can be very useful. The password is usually set using the CMOS Setup utility or various additional programs launched from the AUTOEXEC BAT autoconfiguration file. We'll tell you how to do this using Award Software's Setup, a program stored in the ROM of most PCs. So, turn on the computer and, by pressing the [Del] key, enter Setup. Select “BIOS Features Setup” from the menu that appears, and then “Security Options”. Make sure this option is set to "System" (the password applies to the entire system). If set to "Setup" (only the configuration program is protected), change it with the [PgDn] key. After this, press the [Esc] key to return to the main menu. Select the "Password Setting" item in it. In the window that appears, enter your password and press the [Enter] key. The program will prompt you to do this again, thereby confirming your intentions. Then exit Setup and save the changes made (the "Save & Exit Setup" item in the main menu). The computer will restart and you will be asked to enter your password. Without doing this, you will not be able to continue working. This request will be repeated every time you turn on the computer, as well as after pressing the "RESET" button or the [Ctrl]+[Alt]+[Del] key combination. In the same way, you can change or completely cancel your password. But now you can start Setup only using the already set password. Once in the familiar "Password Setting" mode, enter a new code word, and if you want to remove the protection without entering a new value, press the [Enter] key. Keep in mind that bypassing the password is not at all difficult - just turn off the power to the CMOS memory chip on the computer's motherboard for a short time. True, this will also destroy other settings stored in it (for example, hard disk parameters), and they will have to be entered again using the same Setup program. On ATX standard boards, the power is turned off with a special removable jumper. If it is not there, you have to remove the battery from the socket. But, by the way, many versions of CMOS Setup provide a “universal” password, by entering which you can gain access to a protected computer. In particular, in the reviewed Setup program from Award Software, this is “AWARD_SW” (all letters in uppercase). According to the developers, it should be known only to the company's service personnel. But it is no secret that everything secret becomes clear *. * Knowing that the universal password quickly ceases to be a secret, computer manufacturers periodically change it. Thus, at least nine options are known for Award's BIOS. - Note ed. USER CONFIGURATIONS The Windows 95 operating system gives everyone working on the same computer the ability to create their own system configuration. In the "Shutdown" menu, which appears on the screen before turning off the computer, among other items there is this one - "Log in under a different name." Once you select it, you can enter your name (or nickname), password, and register with Windows 95 as a new user. Now, by providing this data every time you boot the operating system, you can work in a configuration that no one will change without your knowledge. This also prevents unregistered users from accessing Windows, even after passing the first barrier - the CMOS Setup password. Before you create working configurations for each user, you must open the "Control Panel" and select the "Passwords" icon there. Having done this, go to the "Configurations" tab, where set the button with the inscription "Each user can have his own system of settings selected when logging into Windows" to the active state. In the bottom frame of the bookmark, check all the flags (there are two of them). After this, restart Windows. The already mentioned prompt to enter your name and password will appear on the screen. Now you can start creating your own desktop configuration, menus and other Windows elements. Unfortunately, it is much more difficult to organize several user configurations when working with MS DOS or Windows 3.x, but it is still possible. There is, for example, a simple method based on copying different versions of Windows initialization files into the working directory of the environment before starting it. The main disadvantage of MS DOS and Windows 3x, from the point of view of the problem under consideration, is the impossibility of setting passwords using the standard tools of these systems. Therefore, when working in these environments, pay serious attention to setting the CMOS Setup password. PASSWORD AFTER BREAKS During short breaks in work, which happen quite often, the computer is usually not turned off, the time it will take to “wake up” and, for example, loading Windows and opening all documents, may be longer than the duration of the break itself. And in general, frequent switching on and off has a detrimental effect on the “health” of any electronic equipment. How can you protect your computer without turning off the power? After all, in this case, the password to log into the system is useless - it is already running. The problem is solved by screen savers programs that ask for a password when you try to exit them. To install a screen saver in Windows 3, open the "Control Panel" window and click on the "Appearance" icon. In the "Screen Saver" box, select any graphic effect from "Blank Screen" to "Starfield Simulation" from the list. You can pre-evaluate it by clicking the "Test" button. Then, at the bottom of the frame, set the delay time for the screen saver to start, and then click the "Options" button. In the "Password options" frame, check the "Password protection" box and click the "Assign password" button. In the window that appears, enter your secret code twice (in the middle and bottom fields), then click the "OK" button. From now on, you can safely leave your workplace - after a specified time after the last keystroke or mouse manipulation, the screen saver will start. Some programs that extend the capabilities of Windows, such as IconHear-lt, allow you to activate the screen saver without having to wait: just move the mouse pointer to the upper right corner of the screen (if desired, in any other) - and the screen saver screen saver will appear. By the way, such programs are equipped with their own graphic effects, often more attractive than standard Windows screensavers. In Windows 95, the screen saver password is set a little differently. Right-click "mouse" and select "Properties" from the menu that appears. On the "Screen Saver" tab, in the "Monitor Energy Saving Features" frame, clear all flags, and in the "Screen Saver" frame, select a graphic effect from the list (it is displayed in a stylized image of a computer monitor, but you can see it in full screen using the "View" button) . In the right part of the frame, activate the "Password" flag and click the "Change" button. Enter the password twice (in the upper and lower fields) and click OK. A message will appear on the screen: "Password has been successfully changed". As in Windows XNUMX.x, after a specified time of inactivity of the keyboard and mouse, the screen saver program will start working. Packages like Microsoft PLUS! and Microsoft Power Toys, allow you to similarly IconHear-lt to set the corner of the screen, when you move the mouse cursor to which the splash screen appears immediately. They have, of course, their own graphic effects. Unfortunately, all the tools described above only work under Windows. But what about MS DOS users? The popular Norton Commander version 5.0 shell has a lot of screen savers, but the ability to protect exit from them with a password is not provided. Do not install Windows specifically in order to use a screen saver with a password! Full-fledged screen savers for DOS still exist, but it is very difficult to find them, like other useful programs for this operating system: the market is filled with software only for Windows 95/98. Without further ado, it is better to write your own program that performs the desired operation. This is easy to do, for example, using the QuickBASIC programming system. The text of the program of one of the possible options for a password-protected screen saver is shown in the table. It is easy to see that this is a slightly modified version of the program from the author's article "Typical template of a program module in a high-level language" ("Radio", 1998, No. 1, p. 22, 23). Therefore, we will not dwell on it in detail, we will note only some important points. In response to the prompt to set a password, you must enter any set of letters and numbers and press the [Enter] key. Do this carefully, since there is no opportunity to correct the error (however, the author's task is to suggest an idea, and readers can improve the program). Then you can safely leave. To exit the store, you must enter the same password again. If it does not match the specified one, then after the second attempt to enter it, a sound signal will sound (like a siren) and the computer will "freeze". If, when compiling the program, it was not possible to stop its work by pressing [Ctrl] + [Break], it will be possible to return the computer to working condition only by the three-key combination [Ctrl] + [Alt] + [Del] or by pressing the "RESET" button. As a result, another password prompt will appear on the screen - this will be done by the CMOS Setup program. The screensaver executable is best given a short name, such as S.EXE. To run it (if the appropriate path is set in AUTOEXEC.BAT), just press two keys: [S] and [Enter]. A beautiful option is to connect your keeper to the Norton Commander 5.0 shell, in the menu of which "Commands" - "Configuration" - "Screen blanking" you need to select an arbitrary graphic effect (which one does not matter, the keeper still uses its own) and set the delay time . The program file should be called SAVER.EXE and replaced with the one of the same name in the working directory of the shell (usually NC).
DATA ENCRYPTION None of the recommendations of the previous sections will help if the computer is "hacked" by a professional who will only be irritated by all sorts of passwords. When data needs to be kept secure, protect and encrypt the files that contain it, not the entire computer. This article deliberately does not cover such features as setting passwords for opening documents in a Word text editor or unpacking archives using the ARJ program, home-made encryption algorithms, and other methods that protect data only from mediocre curiosity. For reliable protection that is not amenable to professional crackers, it is necessary to use only professional tools. One of them is the encryption of information using the DES algorithm, which is the basis of one of the US federal standards and domestic GOST 28147-89. It is implemented by many fairly popular programs, including PCSecure from the PC Tools package, PGP, widely known on the Internet, and the Diskreet utility from Norton Utilites. Let's take a closer look at Diskreet for MS DOS, the most well-known and accessible tool for domestic users. This utility offers two encryption methods. With its help, you can encrypt individual files or organize a secret logical disk (NDisk) on the hard drive, where all data will be stored in encrypted form. The wide possibilities of this program cannot be described in a short magazine article, so we will only talk about the basic ones required for reliable encryption of important data. When you run the DISKREET.EXE file, you may see a message stating that the DISKREET.SYS driver is not installed. If you don't need to create a secret disk, then you don't need it, and you can set the "Disable This Message" flag in the message box. A similar result can be achieved by deselecting the "Warn if Driver Not Loaded" flag in the "Options" - "Global" menu. Now let's set the encryption parameters. In the "Options" - "File" menu, Diskreet offers two algorithms: simplified ("Fast Proprietary Method") and DES ("Government Standard"). The latter is slower, but more reliable (if you need a high degree of protection, use DES encryption). In the same window, enable the options "Delete original files after encryption" and "Use same password for entire session" and click " save". Go to the menu "Options" - "Global", set the method for deleting source files ("Data Clearing Method"). To prevent anyone from recovering them, it is best to use the "Government Wipe (DOD Spec)" ("DoD-standard wipe"). To encrypt a file or a group of files, use the "File" - "Encrypt" menu. In the window that appears, select the files to be encrypted (text documents, databases, program executable codes, etc.). In this case, you can switch to another disk, browse directories, use masks (symbols * and ?). When prompted on the screen, enter the encryption key, then confirm it and be sure to write it down somewhere (on paper) because, unlike CMOS Setup or Screen Saver passwords, which can be bypassed, data can be decrypted without knowing the correct key. it won't work. Choose it to be no shorter than eight characters, otherwise the code will be easy to guess. Do not use your phone number, car number, passport number, initials or similar data of relatives, friends and acquaintances as part of the key. Decryption specialists begin selecting keys with these options. The more meaningless the set of characters, the better, however, as they say, do not overdo it: a code like "D^al'OSkq" will be forgotten within a minute after entering! By default, Diskreet assigns the SEC extension (from the words "secret" or "security") to all encrypted files, and erases the originals. Decrypt data using the "File - Decrypt" menu of the same program. Files are selected in the same way as it was done during encryption. After pressing the "OK" button, you must enter the encryption key. Of course, the key to any cipher, even the most complex one, can be found as old as the world by trying all combinations - after all, a computer uses only 256 characters, of which a maximum of 240 are available to form a key. In the relevant organizations, powerful computers are used to decrypt, checking hundreds options per second. Nevertheless, the described method quite reliably protects data from competitors who do not have unlimited capabilities. STORAGE OF CONFIDENTIAL INFORMATION If you do not want outsiders to dig into your data, even if it is classified in all possible ways, do not give them such an opportunity - do not store anything but programs on your hard drive! There are quite a lot of removable media suitable for storing large amounts of data: these are ordinary floppy disks and more capacious Zip drives, expensive but reliable Jaz, various magneto-optical disks, streamers, rewritable CDs and much more - choose depending on your goals and financial opportunities. However, even something as simple as storing data on removable media should be handled with special responsibility when it comes to confidential information. Each file must be written to at least two different media (in other words, each disk must have a copy) and stored in different, moderately remote locations. If something happens to one of them (fire or ordinary theft), you can count on the fact that all the information remained safe and sound elsewhere. Of course, data on removable media must be encrypted. Now - about the specifics of working on a computer with confidential information. If the removable media you are using is fast enough, try not to copy sensitive data files to your hard drive at all.** If it was not possible to do without a hard drive, at the end of work, be sure to destroy all data files on it. It makes no sense to do this using standard MS DOS tools, since the DEL command does not actually erase data, but only makes it possible to write new ones in their place. If no records have been made, the deleted file can be easily recovered - a special UNDELETE command is provided for this. But even after writing new data, large pieces of "deleted" information often remain on the disk, which is not difficult to read. For DOS, use the Wipeinfo program from the Norton Utilities package to remove sensitive data. It completely erases the deleted information from the disk and makes it impossible to restore it. Instead, you can use the SpeeDisk or DEFRAG utilities. Any of them in the modes "Unfragment Files Only" ("Only defragment files") and "Full Optimization" ("Full optimization"), in addition to fulfilling its main task - optimizing the placement of data on the disk, completely erases everything related to deleted in the usual way files.*** In Windows 95, no action needs to be taken to erase deleted files. Do not forget only at the end of the work to "take out the trash" - by selecting the "Trash" icon on the desktop (in the English version - "Recycled", which means "recyclable"), destroy its contents. ** Many programs, such as word processors, create temporary files on the hard drive as they run. Moreover, the Windows operating system itself periodically writes data that does not fit in RAM to the so-called "paging file". Although all these files are automatically destroyed, traces of secret data may still remain on the "hard drive" (Ed. note). *** This is not entirely true. If large files were deleted that were at the end of the occupied disk space (i.e., recently recorded), then after defragmentation, some of the data they contained will most likely still remain on the disk (Editor's note). Author: A. Lomov, Moscow; Publication: N. Bolshakov, rf.atnn.ru
Artificial leather for touch emulation
15.04.2024 Petgugu Global cat litter
15.04.2024 The attractiveness of caring men
14.04.2024
▪ Smart hydrogel for XNUMXD printing ▪ Battery Power System for NB-IoT Wireless LTE Module ▪ Microsoft will decipher the human immune system
▪ section of the site Encyclopedia of radio electronics and electrical engineering. Article selection ▪ article Store as the apple of an eye. Popular expression ▪ article What is the principle of thermal insulation? Detailed answer ▪ Bartender article. Job description ▪ article Magic wand acrobat. Focus Secret
Home page | Library | Articles | Website map | Site Reviews www.diagram.com.ua |






 Arabic
Arabic Bengali
Bengali Chinese
Chinese English
English French
French German
German Hebrew
Hebrew Hindi
Hindi Italian
Italian Japanese
Japanese Korean
Korean Malay
Malay Polish
Polish Portuguese
Portuguese Spanish
Spanish Turkish
Turkish Ukrainian
Ukrainian Vietnamese
Vietnamese
 Leave your comment on this article:
Leave your comment on this article: