Thyristor-based car electronic ignition unit

Encyclopedia of radio electronics and electrical engineering /
Automobile. Electronic devices
 Comments on the article
Comments on the article
The thyristor-based electronic ignition block brought to the attention of readers was developed on the basis of a similar block proposed by E. Zubov (see the article "Simplified ignition system", "Radio", 1968, No. 10, pp. 44-45). To improve efficiency, you
rectifier, a diode bridge was introduced into the new block (Fig. 1), and in order to avoid adjustment in the future, a resistor with a resistance of 3,3 kOhm was included in the control electrode circuit of the thyristor and the ratings of some elements were changed.
During the operation of the ignition unit, the direct current from the vehicle's on-board network is converted into alternating current using a generator assembled on transistors

T1 and T2 and transformer Tp1. At the same time, its voltage rises from 12 to 240 V. After the conversion, the alternating current is again rectified by the diode rectifier D1-D4. The rectified current charges the capacitor C2. Thyristor D6 is closed until a positive pulse is applied to its control electrode. Such a pulse is applied to the thyristor from the capacitor C1 through the diode D5 at the moment of breaking the breaker contacts. The thyristor opens and closes the rectifier bridge and capacitor C2 to the case. Capacitor C2 is discharged through the thyristor and the primary winding of the ignition coil, creating a high voltage pulse in the secondary winding. While the thyristor is open, the converter does not work, and there is no voltage at the output of the bridge. Therefore, as soon as the discharge of capacitor C2 ends, the thyristor is locked. From the same moment, the converter resumes operation, and the block operation cycle is repeated.
If necessary, by simply switching switches B1 and B2, the car can be switched from electronic ignition to conventional.
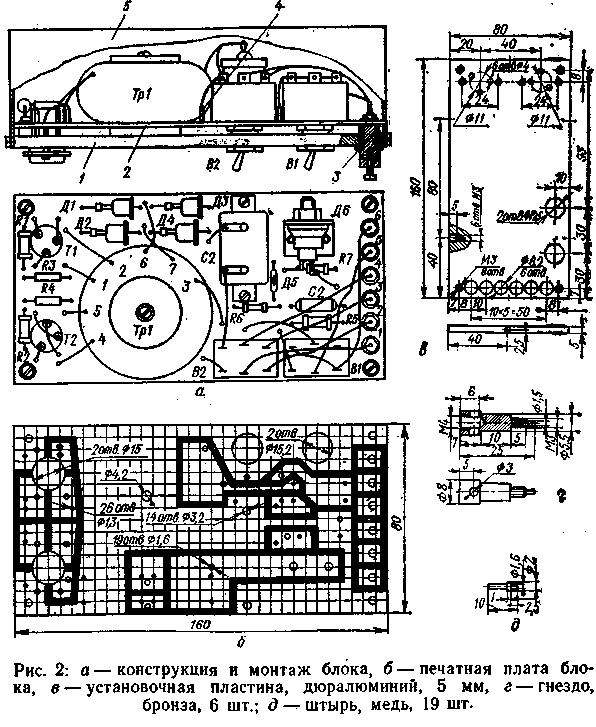
The design and installation of the block are illustrated in fig. 2. The connections shown in the figure are made with an insulated single-core installation wire, for example,
PMV 0,5. The remaining connections are obtained by desoldering the elements on the printed circuit board. When assembling the block, the mounting plate 2 (Fig. 2,6) is installed to the plate 1 (Fig. 2, c) with the foil side. Pins. 4 (Fig. 2, (3) are inserted with short ends into holes with a diameter of 1,6 mm on the board. The ends of the pins are riveted and soldered. After installing and soldering all the parts, the board is coated on both sides with a transparent zapon varnish (nitroglyptal varnish can also be used).
To the case (drawings are not provided for it), the block is attached at the ends of the plate with six M3 screws. For tightness, the gaps at the passage through the nest plate 2 (Fig. XNUMX, d) are filled with varnish. When installing the unit on a car, the plate must have a reliable electrical connection with the body.
Details. Resistors MLT-1 and MLT-0,25 are used in the ignition unit. Capacitor C1 is BM-1, and C2 is MBGO for 300 V. Diodes D226 can be replaced by D7Zh, diode D9V by any pulsed diode, and transistors P216 by MP4V or MP4G. When replacing, be aware of the installation dimensions, which are determined by the printed circuit board.
The Tpl transformer is made on a core of two ferrite rings K40X 25X7,5 of the 2000 NM brand folded together. Winding I between terminals 1-2 contains 20 turns of PEV wire 0,31; between terminals 2-3-4-90 +90 turns of PEV wire 0,9; 4-5-20 turns of the same wire. Winding II (pins 6-7) has 1800 turns of wire PEV 0,2 or PELSHO 0,2.
The circuit board (Fig. 2,6) is made by a photochemical method. But if only one copy is required, then it is easier to transfer the drawing from fig. 2,6 (grid pitch - 5 mm) and remove blackened areas.
A properly assembled block does not require adjustment, it starts working immediately. When checking the assembled unit, it is necessary to ensure that the spark gap in the boost winding circuit of the ignition coil does not exceed 10 mm, otherwise the insulation in the coil may break through.
Author: A. Blagoveshchensky; Publication: cxem.net
See other articles Section Automobile. Electronic devices
 Read and write useful comments on this article.
Read and write useful comments on this article.
<< Back
 Latest news of science and technology, new electronics:
Latest news of science and technology, new electronics:
Air trap for insects
01.05.2024
Agriculture is one of the key sectors of the economy, and pest control is an integral part of this process. A team of scientists from the Indian Council of Agricultural Research-Central Potato Research Institute (ICAR-CPRI), Shimla, has come up with an innovative solution to this problem - a wind-powered insect air trap. This device addresses the shortcomings of traditional pest control methods by providing real-time insect population data. The trap is powered entirely by wind energy, making it an environmentally friendly solution that requires no power. Its unique design allows monitoring of both harmful and beneficial insects, providing a complete overview of the population in any agricultural area. “By assessing target pests at the right time, we can take necessary measures to control both pests and diseases,” says Kapil ... >>
The threat of space debris to the Earth's magnetic field
01.05.2024
More and more often we hear about an increase in the amount of space debris surrounding our planet. However, it is not only active satellites and spacecraft that contribute to this problem, but also debris from old missions. The growing number of satellites launched by companies like SpaceX creates not only opportunities for the development of the Internet, but also serious threats to space security. Experts are now turning their attention to the potential implications for the Earth's magnetic field. Dr. Jonathan McDowell of the Harvard-Smithsonian Center for Astrophysics emphasizes that companies are rapidly deploying satellite constellations, and the number of satellites could grow to 100 in the next decade. The rapid development of these cosmic armadas of satellites can lead to contamination of the Earth's plasma environment with dangerous debris and a threat to the stability of the magnetosphere. Metal debris from used rockets can disrupt the ionosphere and magnetosphere. Both of these systems play a key role in protecting the atmosphere and maintaining ... >>
Solidification of bulk substances
30.04.2024
There are quite a few mysteries in the world of science, and one of them is the strange behavior of bulk materials. They may behave like a solid but suddenly turn into a flowing liquid. This phenomenon has attracted the attention of many researchers, and we may finally be getting closer to solving this mystery. Imagine sand in an hourglass. It usually flows freely, but in some cases its particles begin to get stuck, turning from a liquid to a solid. This transition has important implications for many areas, from drug production to construction. Researchers from the USA have attempted to describe this phenomenon and come closer to understanding it. In the study, the scientists conducted simulations in the laboratory using data from bags of polystyrene beads. They found that the vibrations within these sets had specific frequencies, meaning that only certain types of vibrations could travel through the material. Received ... >>
 Random news from the Archive
Random news from the Archive
Fortinet Software Defined Network Security
22.09.2015
Fortinet has introduced a new security system for software-defined networks (Software-Defined Network Security-SDNS). The system provides advanced threat protection in today's flexible data center environment. "This is a clear vision for a comprehensive approach to data center IT security that provides an advanced integration platform with partners such as HP, Ixia, PLUMgrid, Pluribus Networks, Extreme Networks and NTT," Fortinet said.
Security in an SDN environment sets new standards for network security in today's enterprise, where data centers have been completely modified through the use of virtualization technologies, cloud computing and software-defined networking.
"Often, the information security infrastructure is too static, which prevents it from responding to the rapidly changing needs of the digital economy and effectively preventing ever-changing threats," said Neil MacDonald, vice president and noted analyst at Gartner Research. "Increasingly, network security vendors are replacing individual pieces of hardware to control software to achieve flexibility in security policies, regardless of location."
According to the developers, Fortinet's new SDN security system brings innovations to all major layers of the network architecture: Data plane - combining security services from hardware modules into logical entities, providing additional scalability and tight integration into the switching fabric and network flows; Control plane - control and automate the processing of security policies with adaptive load balancing to eliminate delays in ensuring security and compliance in dynamic environments; Management plane - centralized management of security policies and events of physical and virtual applications, private and public "clouds" throughout the infrastructure to ensure comprehensive security.
"We don't think there will be a single, standard SDN platform that all enterprises and service providers will use," said John Madison, vice president of marketing at Fortinet. "That's why we're building a partner ecosystem to support a variety of SDN platforms through our own and open application programming interfaces (APIs). It is important to provide scalable security modules that can be used and converted on demand."
Fortinet's software-defined networking security efforts began more than five years ago with the first FortiGate-VM virtual appliances designed to protect virtualized and consolidated data centers. These efforts have continued concurrently with the ongoing transformation of the data center. As part of its data center strategy, the company works closely with a growing number of partners to provide the right protection for their key infrastructures. These platforms include SDN controllers, orchestration bases, hypervisors, cloud management, security management, and analytics. Fortinet is currently working with two dozen vendors to provide cyber security protection with an advanced SDN security platform.
|
 News feed of science and technology, new electronics
News feed of science and technology, new electronics
 We recommend downloading in our Free technical library:
We recommend downloading in our Free technical library:
▪ site section Electrician's Handbook
▪ magazines KV magazine (annual archives)
▪ Antenna book. Rothammel K., 1979
▪ article by Rabindranath Tagore. Famous aphorisms
▪ article Power supply. Surge Protectors. Directory
▪ article Self box. Focus Secret
▪ reference book Service menus of foreign TVs. Book #13
 Leave your comment on this article:
Leave your comment on this article:
 All languages of this page
All languages of this page
Home page | Library | Articles | Website map | Site Reviews

www.diagram.com.ua
2000-2024








 Arabic
Arabic Bengali
Bengali Chinese
Chinese English
English French
French German
German Hebrew
Hebrew Hindi
Hindi Italian
Italian Japanese
Japanese Korean
Korean Malay
Malay Polish
Polish Portuguese
Portuguese Spanish
Spanish Turkish
Turkish Ukrainian
Ukrainian Vietnamese
Vietnamese
 Leave your comment on this article:
Leave your comment on this article: